Encrypting User Devices #
There are three levels to device encryption:
- Practice Level
- Office Level
- User level
Steps to Encrypt User Devices:
- Enable Device Encryption against the Support email through Settings → Practices.
- Enable Device Encryption for the Practice through Settings → Practices.
- Add the User’s Device to the User Devices table. This can be done using one of the following methods:
Method 1: Accept a Login Request from the Login Page.
Method 2: Manually Add a Device by entering the Visitor ID in User Devices.
Purpose: This allows encryption of specific devices with access to Legend, ensuring HIPAA and patient privacy compliance.
Only authorized devices will be permitted to log in to safeguard sensitive information. This prevents employees from accessing the system on unauthorized devices, such as personal phones or external computers.
1. Enable Device Encryption against the Support email #
- Navigate to Settings -> Practices -> Manage Locations
- Click on the Edit icon against the Office of the required Location
- Add a valid Support email
- Check the Encrypt Specific Devices checkbox
- Click on the Update Location button
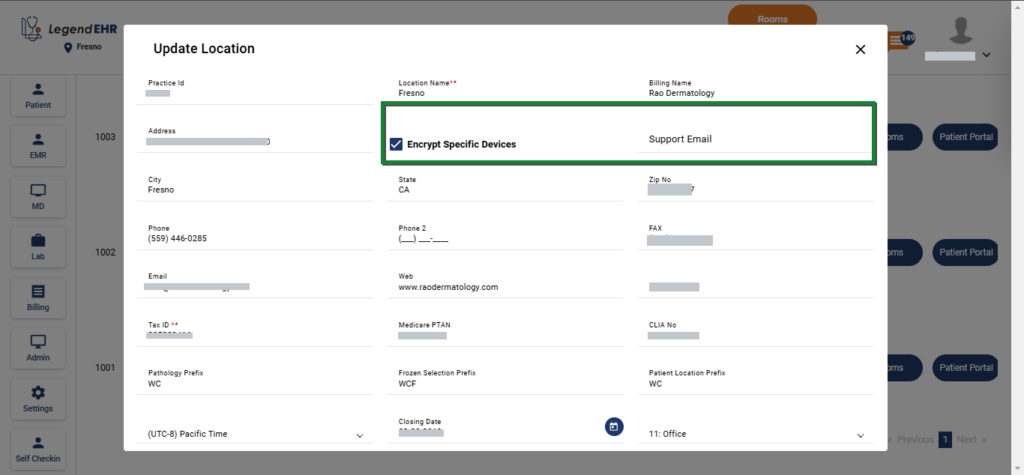
The Support email will be used to receive a login request if the Enable Specific Devices checkbox is checked.
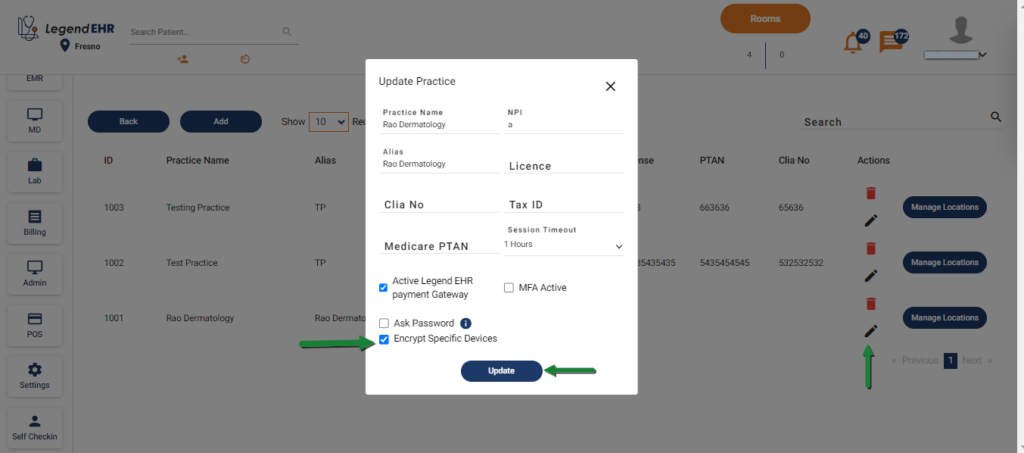
2. Enable Device Encryption for the Practice #
- Navigate to Settings -> Practices -> Edit
- Check the Encrypt Specific Devices checkbox
- Click on the Update button
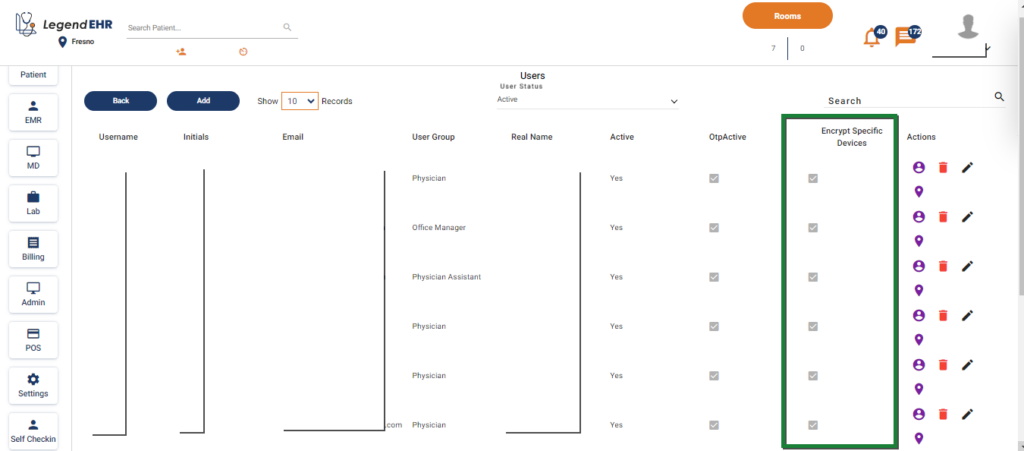
- Go to Settings → Users
- Checkboxes against all the users are checked for the Encrypt Specific Devices
In this manner, all user devices are now required to be encrypted, and users will be unable to log in until the device they intend to use has been successfully encrypted and registered with the system.
Users are now unable to log in if encryption is enabled.
Note: Encryption will only be applied if it is enabled for the entire practice through Settings → Practices → Edit and it will not activate if enabled solely from the Locations settings.
Remove Encryption For a specific User/Location
- To disable device encryption for a user, simply uncheck the “Encrypt Specific Devices” checkbox. This will allow the user to log in from any device.
2. To disable device encryption for a Location, simply uncheck the “Encrypt Specific Devices” checkbox for that Location. This will allow the user to log in from that location with any device.

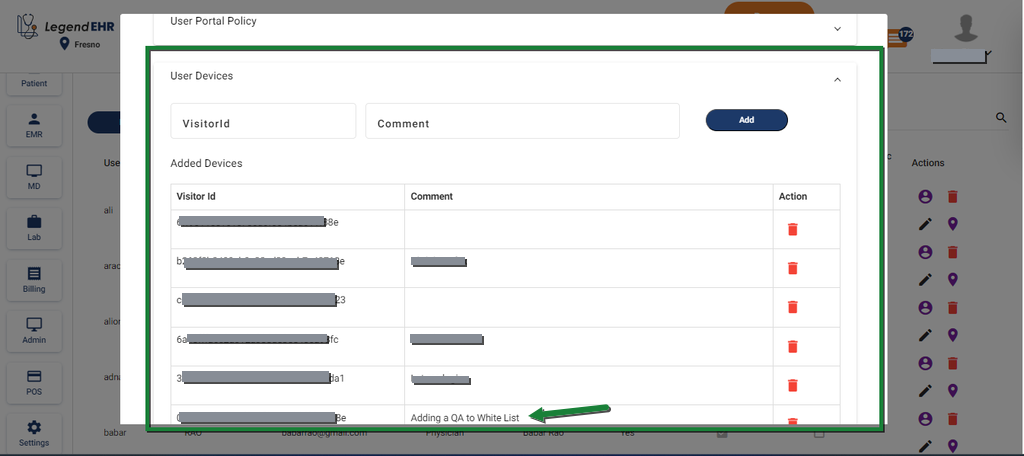
3. Add the User’s Device to the User Devices #
To encrypt their device, you can follow either Method 1 or 2 outlined below:
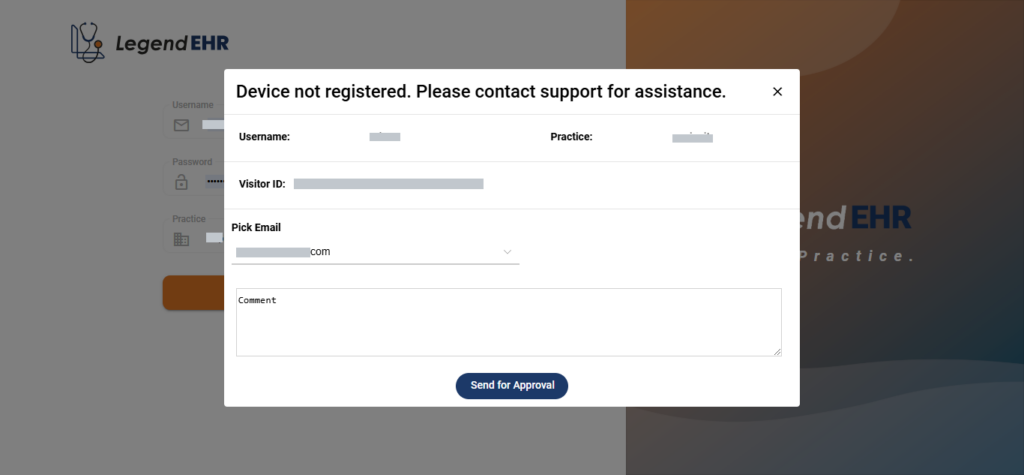
Method 1: Accept a Login Request from the Login Page: #
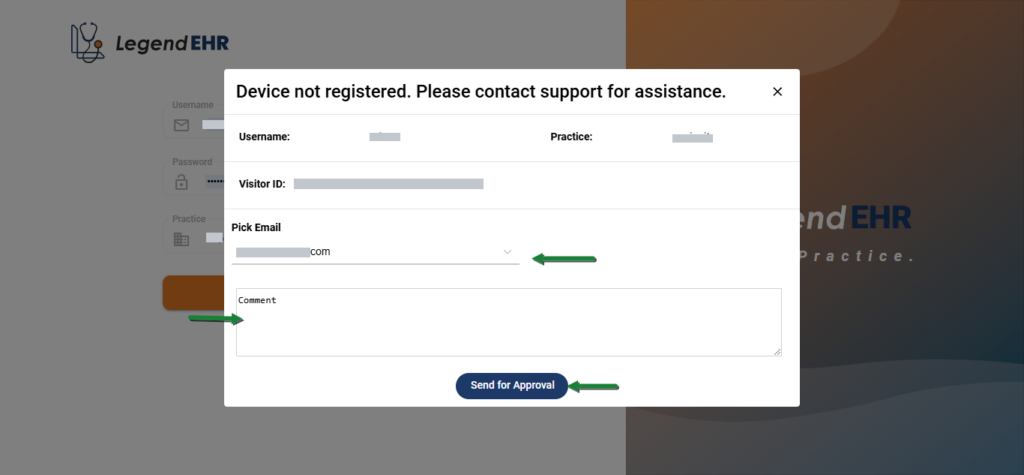
There is an email dropdown in the Login Request popup on the Login page, where Support emails of all the Locations appear where the user has access, provided the Encrypt Specific Devices checkbox for Locations is checked.
- The User will select an email from the dropdown to send a request to
- He can write a Comment
- Then click on the Send for Approval button
- An email will be received on the Support Email selected by the User for approval
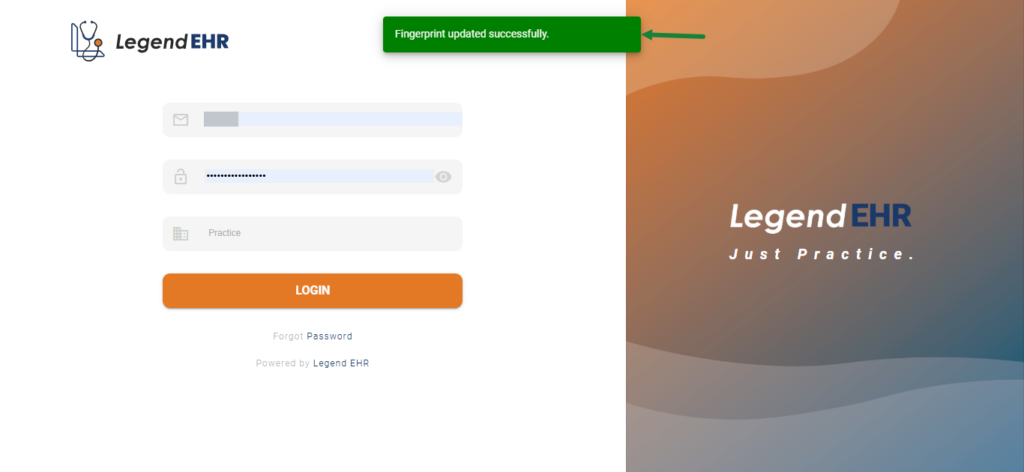
- The Support Team will approve the request

Once the request is approved, the User’s Fingerprint is updated successfully.
This will add the user’s device to the whitelist table under Settings → Users → Edit → User Devices dropdown. When a user sends a login request while encryption is enabled, and the system successfully authenticates the request, the user’s device will be securely registered and added to the whitelist. This ensures that the user can only log in from this verified device while encryption remains enabled.
Method 2: Manually Add a Device by entering the Visitor ID in User Devices: #
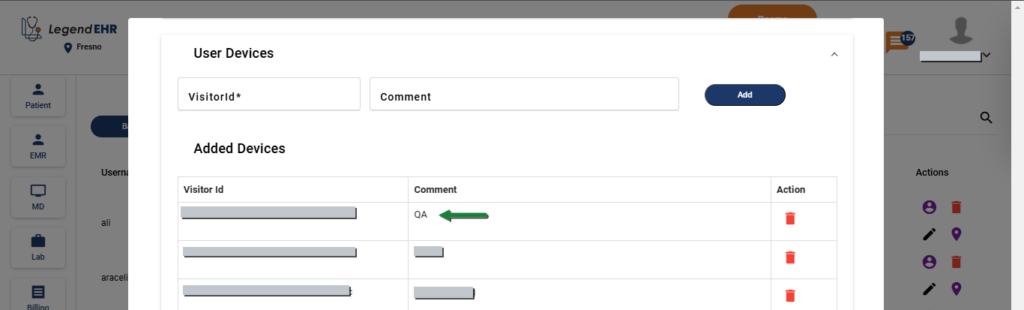
- Go to Settings → Users → Edit → User Devices dropdown
- Write the Visitor ID of the requester
- Write the details in the comment
- Click on the Add button
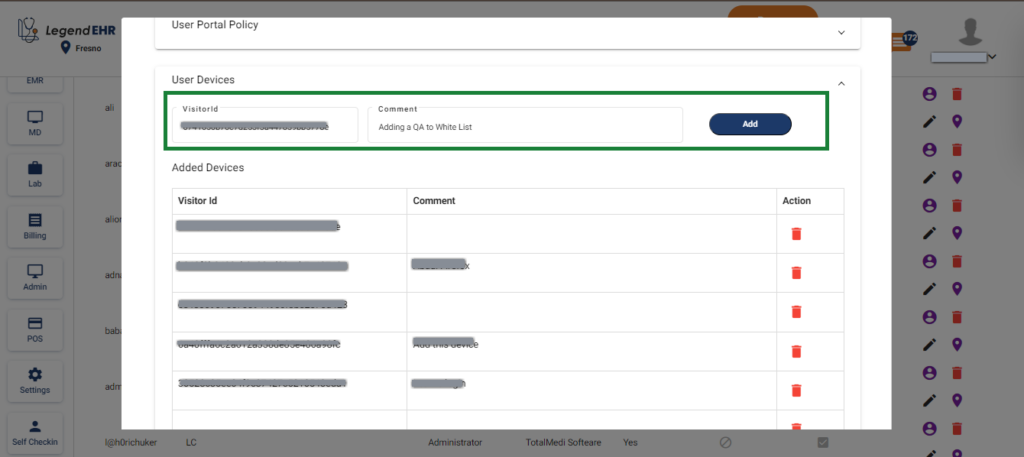
This will add the user’s device to the whitelist table under Settings → Users → Edit → User Devices dropdown. As a result, the user will only be able to log in from the device whose Visitor ID has been securely registered in the User Devices table. This restriction ensures that, while encryption is enabled, the user cannot log in from any unregistered device.